Nfsen is open source sensor: it accepts netflow data from multiple netflow probes (servers, routers, vpn concentrators etc) and then visualizes it into human readable form. So using Nfsen you can see traffic statistics of every network device in your network in one place (actually Nfsen provides much more features).
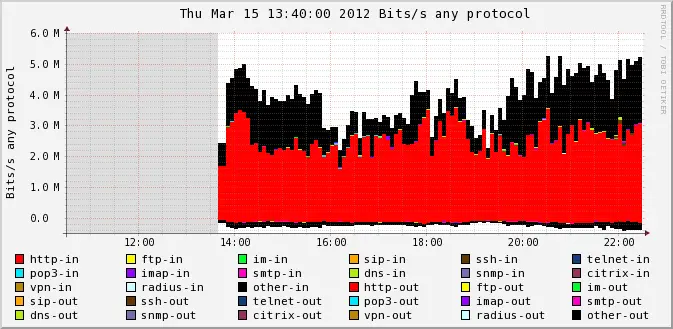
By default Nfsen makes it possible to see only inbound and outbound traffic statistics but no protocol breakdown or any traffic classification. In the meantime it’s always useful to know what network applications are eating the bandwidth to understand if that fits baseline or not and take necessary actions. For example, if you’re monitoring Linux server which primary task is to host some website but in Nfsen you see that it generates 90% of SSH traffic and only 10% of web traffic then it would be reasonable idea to check if somebody is trying to brute force SSH password and stop that activity. In other words it’s better to have traffic statistics classified. In this article I’ll tell you how to enable traffic classification in Nfsen.

![Using the SCP Command to Securely Copy Files [Examples] 1 Using the SCP Command](https://cd.linuxscrew.com/wp-content/uploads/2020/12/Using-the-SCP-Command-300x194.png)

![How to Use the Dig Command [With Examples] 3 How to Use the Dig Command](https://cd.linuxscrew.com/wp-content/uploads/2020/12/How-to-Use-the-Dig-Command-300x194.png)